Discrete Logarithm Cryptography (DLC)
[API]
Fundamental declarations and definitions for algorithms based on discrete logarithm problem. More...
Data Structures | |
| struct | C4eDlcDomain |
| Discrete logarithm (DL) domain parameters (public). More... | |
Modules | |
| DLC Temp. Space Qualifiers | |
Temp. space qualifiers for DL based cryptography (exclusive RSA). | |
| Diffie-Hellman (DH) | |
Diffie-Hellman shared secret computation in discrete logarithm (DL) domain. | |
| Digital Signature Algorithm (DSA) | |
Digital Signature Algorithm (DSA) in discrete logarithm (DL) domain. | |
Defines | |
| #define | C4E_DLC_GF_BYTES_MAX |
| Maximum allowed size (in bytes) of a discrete logarithm (DL) domain modulus in C4eDlcDomain::m. | |
Functions | |
| C4eSysStatus | c4e_dlc_domchk (C4eArchUint algos, C4E_CONST C4eDlcDomain *dom) |
| A simple (and fast) discrete logarithm domain parameters validity test. | |
| C4eSysStatus | c4e_dlc_keychk_prv (C4eArchUint algos, C4E_CONST C4eDlcDomain *C4E_RESTRICT dom, C4E_CONST C4eElement *C4E_RESTRICT key, C4eArchDigit tmp[C4E_RESTRICT]) |
| Discrete logarithm (DL) domain private key validity test. | |
| C4eSysStatus | c4e_dlc_keychk_pub (C4eArchUint algos, C4E_CONST C4eDlcDomain *C4E_RESTRICT dom, C4E_CONST C4eElement *C4E_RESTRICT key, C4eArchDigit tmp[C4E_RESTRICT]) |
| Discrete logarithm (DL) domain public key validity test. | |
DLC Algorithm Identifiers | |
Algorithm identifiers for Discrete Logarithm Cryptography (DLC), to be used as parameter to c4e_dlc_domchk(). | |
| #define | C4E_DLC_ALGO_NONE |
| "unspecific" algorithm identifier. | |
| #define | C4E_DLC_ALGO_DH |
| DH algorithm identifier. | |
| #define | C4E_DLC_ALGO_DSA |
| DSA algorithm identifier. | |
| #define | C4E_DLC_ALGO_RSA |
| RSA algorithm identifier. | |
| #define | C4E_DLC_ALGO_ALL |
| "all" algorithm identifier. | |
Detailed Description
Fundamental declarations and definitions for algorithms based on discrete logarithm problem.
Define Documentation
| #define C4E_DLC_GF_BYTES_MAX |
Maximum allowed size (in bytes) of a discrete logarithm (DL) domain modulus in C4eDlcDomain::m.
- Customize:
- Simply undefine C4E_DLC_GF_BYTES_MAX to support longer (unlimited) modulus sizes. Modify it if you want to limit the size of a modulus to this value (recommended for static memory reservation).
Function Documentation
| C4eSysStatus c4e_dlc_domchk | ( | C4eArchUint | algos, | |
| C4E_CONST C4eDlcDomain * | dom | |||
| ) |
A simple (and fast) discrete logarithm domain parameters validity test.
Function c4e_dlc_domchk() checks the following conditions:
- The modulus
dom->m.valmust be odd and greater than zero. - The size of modulus
dom->m.valmust be less thanC4E_ELEM_DIGITS_NUM(dom->m.len). - The field size
dom->m.lenmust be less/equal C4E_DLC_GF_BYTES_MAX (if defined).
If algos does contain C4E_DLC_ALGO_DSA then the following additional conditions are checked:
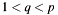 , q an odd number;
, q an odd number;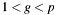 ;
;- the size
dom->q.val.sizefits C4E_ELEM_DIGITS_NUM(dom->q.len); - the size of
dom->m.valis at least:2U * C4E_MODN_POW_SPACE(dom->q.val.size)
- Note:
- This test is not fully conforming to IEEE Std 1363, annex A.16.2, FIPS 186-4, annex A.1.2.2 and NIST SP800-89, section 4. Especially condition #7 of FIPS 186-4, annex A.1.2.2 is not checked:
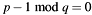 .
.
- Precondition:
- All big numbers in
dommust be normalized, for example by using functions c4e_elem_norm() or c4e_elem_os2e().
- Bibliography:
Standard Specifications For Public-Key Cryptography. Std 1363-2000, IEEE, 2000.
Digitale Signature Standard (DSS). FIPS Publication 186-4, National Institute of Standards and Technology, 2013.
NIST Special Publication 800-56A Revision 2: Recommendation for Pair-Wise Key Establishment Schemes Using Discrete Logarithm Cryptography. 2013.
NIST Special Publication 800-89: Recommendation for Obtaining Assurances for Digital Signature Applications. 2006.
- Parameters:
-
[in] algos Algorithm identifiers to check domain parameters for (or'ed together). [in] dom Pointer to domain parameters.
- Returns:
- Validity status of
dom.
- Return values:
-
C4E_STATUS_OK If the domain parameters are usable for all calculations (valid in the sense of this implementation). other If one of the domain parameters is invalid.
- See also:
- C4eDlcDomain
- Todo:
- If CRY4E supports key generation (may be in the future) then implement additional tests according to IEEE Std 1363, annex A.16.2.
| C4eSysStatus c4e_dlc_keychk_prv | ( | C4eArchUint | algos, | |
| C4E_CONST C4eDlcDomain *C4E_RESTRICT | dom, | |||
| C4E_CONST C4eElement *C4E_RESTRICT | key, | |||
| C4eArchDigit | tmp[C4E_RESTRICT] | |||
| ) |
Discrete logarithm (DL) domain private key validity test.
The function validates a private key d with respect to:
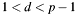 ;
;- if
algosdoes contain C4E_DLC_ALGO_DSA then additionally: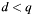 .
.
- Note:
- According to PKCS #3, section 7.1 the allowed range for a private key is:
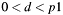 . This has to be required because of Fermats little theorem, which for
. This has to be required because of Fermats little theorem, which for 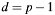 results in:
results in: 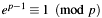 .
.
- Precondition:
- The validity of the DL domain parameters in
dommust be assured by the caller, either implicit or by using function c4e_dlc_domchk(). -
All big numbers in
keyanddommust be normalized, e.g. by using functions c4e_elem_norm() or c4e_elem_os2e().
- Bibliography:
- Standard Specifications For Public-Key Cryptography. Std 1363-2000, IEEE, 2000.
- Bibliography:
- Public Key Cryptography for the Financial Services Industry: Agreement of Symmetric Keys Using Diffie-Hellman and MQV Algorithms (draft), ANSI X9.42, 1998.
- Bibliography:
- NIST Special Publication 800-56A Revision 2: Recommendation for Pair-Wise Key Establishment Schemes Using Discrete Logarithm Cryptography. 2013.
- Bibliography:
- Digitale Signature Standard (DSS). FIPS Publication 186-4, National Institute of Standards and Technology, 2013.
- Parameters:
-
[in] algos Algorithm identifiers to check the private key for (or'ed together). [in] dom Pointer to DL domain parameters. [in] key Private DL key to be tested. tmp Array of dom->m.val.sizetemporary space elements.
- Returns:
- Validity status of
key.
- Return values:
-
C4E_STATUS_OK If the key seems to be valid. other If the key is invalid.
- See also:
- C4eDlcDomain, C4eElement
- Todo:
- If CRY4E supports key generation (may be in the future) then implement additional tests according to NIST SP800-56A.
| C4eSysStatus c4e_dlc_keychk_pub | ( | C4eArchUint | algos, | |
| C4E_CONST C4eDlcDomain *C4E_RESTRICT | dom, | |||
| C4E_CONST C4eElement *C4E_RESTRICT | key, | |||
| C4eArchDigit | tmp[C4E_RESTRICT] | |||
| ) |
Discrete logarithm (DL) domain public key validity test.
The function validates parameter key with respect to:
- the allowed range:
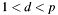 .
.
- Precondition:
- The validity of the DL domain parameters in
dommust be assured by the caller, either implicit or by using function c4e_dlc_domchk(). -
All big numbers in
keyanddommust be normalized, e.g. by using functions c4e_elem_norm() or c4e_elem_os2e().
- Bibliography:
- Standard Specifications For Public-Key Cryptography. Std 1363-2000, IEEE, 2000.
- Bibliography:
- NIST Special Publication 800-56A Revision 2: Recommendation for Pair-Wise Key Establishment Schemes Using Discrete Logarithm Cryptography. 2013.
- Parameters:
-
[in] algos Algorithm identifiers to check the public key for (or'ed together). [in] dom Pointer to DL domain parameters. [in] key Public DL key to be tested. tmp Array of temporary space elements (unused at the moment).
- Returns:
- Validity status of
key.
- Return values:
-
C4E_STATUS_OK If the key seems to be valid. other If the key is invalid.
- See also:
- C4eDlcDomain, C4eElement
- Todo:
- If CRY4E supports key generation (may be in the future) then implement additional tests according to NIST SP800-56A.
 1.6.1
1.6.1