ECC over binary field
[Elliptic Curve Cryptography (ECC)]
Modules | |
| Binary Field EC Temp. Space Qualifiers | |
Temp. space qualifiers for EC based cryptography over binary field. | |
| EC Diffie-Hellman (ECDH) over binary fields | |
Diffie-Hellman shared secret computation in elliptic curve (EC) domain over binary field | |
| Elliptic Curve Digital Signature Algorithm (ECDSA) | |
Elliptic Curve Digital Signature Algorithm (ECDSA). | |
Functions | |
| C4eSysStatus | c4e_ecc2n_domchk (C4eArchUint algos, C4E_CONST C4eEcDomain *dom, C4eArchDigit *C4E_RESTRICT tmp) |
A simple (and fast) domain parameter validity test for elliptic curves over binary field  . . | |
| C4eSysStatus | c4e_ecc2n_keychk_prv (C4eArchUint algos, C4E_CONST C4eEcDomain *C4E_RESTRICT dom, C4E_CONST C4eElement *C4E_RESTRICT d, C4eArchDigit tmp[C4E_RESTRICT]) |
Elliptic curve (EC) over binary field  private key validity test. private key validity test. | |
| C4eSysStatus | c4e_ecc2n_keychk_pub (C4eArchUint algos, C4E_CONST C4eEcDomain *C4E_RESTRICT dom, C4E_CONST C4eEcPoint *C4E_RESTRICT q, C4eArchDigit tmp[C4E_RESTRICT]) |
Elliptic curve (EC) over binary field  public key validity test. public key validity test. | |
| C4eArchSize | c4e_ecc2n_pt2os (C4E_CONST C4eEcDomain *C4E_RESTRICT dom, C4E_CONST C4eEcPoint *C4E_RESTRICT pt, C4eArchUint ptfmt, C4eArchDigit tmp[C4E_RESTRICT], C4eArchSize bufsize, C4eArchUint8 *C4E_RESTRICT buf) |
| Elliptic curve point to octet string conversion primitive, according to ANSI X9.63, section 4.3.6 and 4.2.2 and IEEE Std 1363, section A.9.6 and annex E.2.3. | |
| C4eSysStatus | c4e_ecc2n_os2pt (C4E_CONST C4eEcDomain *C4E_RESTRICT dom, C4E_CONST C4eArchUint8 *C4E_RESTRICT osp, C4eArchSize len, C4eArchDigit tmp[C4E_RESTRICT], C4eEcPoint *C4E_RESTRICT pt) |
| Octet string to elliptic curve point conversion primitive, according to ANSI X9.63, section 4.3.7 and 4.2.2 and IEEE Std 1363, section A.9.6 and annex E.2.3. | |
Binary Field ECC Algorithm Identifiers | |
Algorithm identifiers for ECC over binary field | |
| #define | C4E_ECC2N_ALGO_NONE |
| "unspecific" algorithm identifier. | |
| #define | C4E_ECC2N_ALGO_DH |
| ECDH algorithm identifier. | |
| #define | C4E_ECC2N_ALGO_DSA |
| ECDSA algorithm identifier. | |
| #define | C4E_ECC2N_ALGO_ALL |
| "all" algorithm identifier. | |
Function Documentation
| C4eSysStatus c4e_ecc2n_domchk | ( | C4eArchUint | algos, | |
| C4E_CONST C4eEcDomain * | dom, | |||
| C4eArchDigit *C4E_RESTRICT | tmp | |||
| ) |
A simple (and fast) domain parameter validity test for elliptic curves over binary field  .
.
Function c4e_ecc2n_domchk() checks the following conditions:
- The modulus
dom->m.valmust not be m(x) = 0, not m(x) = 1 and must not have a common (polynomial) factor x. - The size of modulus
dom->m.valmust be less/equal than C4E_ELEM_DIGITS_NUM(dom->m.len). - The field size
dom->m.lenmust be less/equal C4E_EC_GF_BYTES_MAX (if defined). - Curve parameters
dom->aanddom->bmust be less thandom->m.val. - Curve parameter
dom->bmust not be zero (dom->ais allowed to be zero, then elliptic curve E is a Koblitz curve). - The order of base point G in
dom->q.valmust be greater than zero and odd (because #G must be a prime number). - The number of digits in
dom->q.valmust be less than the equivalent value derived fromdom->q.len. - The number of digits in
dom->q.valmust be less than the maximum group order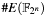 of elliptic curve E (see C4E_EC_FIELD_DIGITS_MAX).
of elliptic curve E (see C4E_EC_FIELD_DIGITS_MAX). - The cofactor
dom->hmust be less thandom->q(only if bit C4E_ECC2N_ALGO_DH set inalgos). - The coordinate values of base point G are in range of underlying ground field
 (only if bit C4E_ECC2N_ALGO_DSA set in
(only if bit C4E_ECC2N_ALGO_DSA set in algos). - The base point G is a field element of elliptic curve E and it is really a base point, satisfying the condition
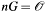 (but only if
(but only if tmpis unequal toNULLand bit C4E_ECC2N_ALGO_DSA set inalgos).
So this function is able to check conditions #1, #2, #4, #5 and #7 of ANSI X9.62 section 5.1.2.2.
- Note:
- In field
 the size of irreducible polynomial m(x) is one bit larger than the maximum size of each field element. Because we do not know the maximum size of a field element in bits (we only know it in bytes) we allow a size for m(x) which is one bit greater than (dom->m.len * 8) bits.
the size of irreducible polynomial m(x) is one bit larger than the maximum size of each field element. Because we do not know the maximum size of a field element in bits (we only know it in bytes) we allow a size for m(x) which is one bit greater than (dom->m.len * 8) bits.
- Precondition:
- The caller may provide temporary memory space in array
tmp[], using macro C4E_ECC2N_TMP_NUM() in conjunction with temp. space qualifier C4E_ECC2N_TMPID_DOM_CHECK. Currently this is needed only if C4E_ECC2N_ALGO_DSA is set inalgosand the base point G must be validated by extended test (see last point of description).
- Bibliography:
- Standard Specifications For Public-Key Cryptography. Std 1363-2000, IEEE, 2000.
- Bibliography:
- Public Key Cryptography For The Financial Services Industry: The Elliptic Curve Digital Signature Algorithm (ECDSA). ANSI X9.62, 1998.
- Bibliography:
- Public Key Cryptography For The Financial Services Industry: Key Agreement and Key Transport Using Elliptic Curve Cryptography. ANSI X9.63, 2001.
- Parameters:
-
[in] algos Algorithm identifiers to check domain parameters for (or'ed together). [in] dom Pointer to domain parameters. tmp Array of temporary space elements (see preconditions for details on size). Currently parameter tmpis allowed to beNULLif C4E_ECC2N_ALGO_DSA is not set inalgosor the extended test should not be performed.
- Returns:
- Validity status of
dom.
- Return values:
-
C4E_STATUS_OK If the domain parameters are usable for all calculations (valid in the sense of this implementation). other If one of the domain parameters is invalid.
- See also:
- C4eEcDomain
- Todo:
- If CRY4E supports key generation (may be in the future) then implement additional tests according to IEEE Std 1363, annex A.16.8 and ANSI X9.63, section 5.1.2.2.
| C4eSysStatus c4e_ecc2n_keychk_prv | ( | C4eArchUint | algos, | |
| C4E_CONST C4eEcDomain *C4E_RESTRICT | dom, | |||
| C4E_CONST C4eElement *C4E_RESTRICT | d, | |||
| C4eArchDigit | tmp[C4E_RESTRICT] | |||
| ) |
Elliptic curve (EC) over binary field  private key validity test.
private key validity test.
The function validates parameter d with respect to:
- the allowed range:
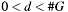 .
.
- Precondition:
- The validity of the EC domain parameters in
dommust be assured by the caller, either implicit or by using function c4e_ecc2n_domchk(). -
All binary polynomials in
dommust be normalized, e.g. by using functions c4e_elem_norm(), c4e_elem_os2e() and/or c4e_ecc2n_os2pt(). -
The private key
d, which is a big number, must be normalized, e.g. by using functions c4e_elem_norm() or c4e_elem_os2e().
- Bibliography:
- Standard Specifications For Public-Key Cryptography. Std 1363-2000, IEEE, 2000.
- Bibliography:
- Public Key Cryptography For The Financial Services Industry: Key Agreement and Key Transport Using Elliptic Curve Cryptography. ANSI X9.63, 2001.
- Parameters:
-
[in] algos Algorithm identifiers to check the private key for (or'ed together). [in] dom Pointer to EC domain parameters. [in] d Private EC key (a big number) to be tested. tmp Array of temporary space elements (unused at the moment).
- Returns:
- Validity status of
d.
- Return values:
-
C4E_STATUS_OK If the key seems to be valid. other If the key is invalid.
- See also:
- C4eEcDomain, C4eElement
| C4eSysStatus c4e_ecc2n_keychk_pub | ( | C4eArchUint | algos, | |
| C4E_CONST C4eEcDomain *C4E_RESTRICT | dom, | |||
| C4E_CONST C4eEcPoint *C4E_RESTRICT | q, | |||
| C4eArchDigit | tmp[C4E_RESTRICT] | |||
| ) |
Elliptic curve (EC) over binary field  public key validity test.
public key validity test.
- Note:
- This function is fully conforming to the "Embedded Public Key Validation Primitive" in ANSI X9.63, section 5.2.2.2 and the simple public key validation test according to IEEE Std 1363, section A.16.10.
- Precondition:
- The validity of the EC domain parameters in
dommust be assured by the caller, either implicit or by using function c4e_ecc2n_domchk(). -
All binary polynomials in
qanddommust be normalized, e.g. by using functions c4e_elem_norm(), c4e_elem_os2e() and/or c4e_ecc2n_os2pt(). -
The caller may provide temporary memory space in array
tmp[], using macro C4E_ECC2N_TMP_NUM() in conjunction with temp. space qualifier C4E_ECC2N_TMPID_KEY_CHECK.
- Bibliography:
- Standard Specifications For Public-Key Cryptography. Std 1363-2000, IEEE, 2000.
- Bibliography:
- Public Key Cryptography For The Financial Services Industry: The Elliptic Curve Digital Signature Algorithm (ECDSA). ANSI X9.62, 1998.
- Bibliography:
- Public Key Cryptography For The Financial Services Industry: Key Agreement and Key Transport Using Elliptic Curve Cryptography. ANSI X9.63, 2001.
- Parameters:
-
[in] algos Algorithm identifiers to check the public key for (or'ed together). [in] dom Pointer to EC domain parameters. [in] q Public EC key to be tested. tmp Array of temporary space elements (see preconditions for details on size).
- Returns:
- Validity status of
key.
- Return values:
-
C4E_STATUS_OK If the key seems to be valid. other If the key is invalid.
- See also:
- C4eEcDomain, C4eEcPoint, c4e_ecc2n_domchk()
- Todo:
- If CRY4E supports key generation (may be in the future) then implement additional tests according to IEEE Std 1363, annex A.16.8 and ANSI X9.63, section 5.1.2.2.
| C4eArchSize c4e_ecc2n_pt2os | ( | C4E_CONST C4eEcDomain *C4E_RESTRICT | dom, | |
| C4E_CONST C4eEcPoint *C4E_RESTRICT | pt, | |||
| C4eArchUint | ptfmt, | |||
| C4eArchDigit | tmp[C4E_RESTRICT], | |||
| C4eArchSize | bufsize, | |||
| C4eArchUint8 *C4E_RESTRICT | buf | |||
| ) |
Elliptic curve point to octet string conversion primitive, according to ANSI X9.63, section 4.3.6 and 4.2.2 and IEEE Std 1363, section A.9.6 and annex E.2.3.
- Precondition:
- The validity of the EC domain parameters in
dommust be assured by the caller, either implicit or by using function c4e_ecc2n_domchk(). -
All binary polynomials in
ptanddommust be normalized, e.g. by using functions c4e_elem_norm(), c4e_elem_os2e() and/or c4e_ecc2n_os2pt(). -
All polynomials in
ptanddommust be normalized, e.g. by using functions c4e_elem_norm() or c4e_elem_os2e(). - The function does not handle the pseudo-point at infinity. Use for example C4E_EC_IS_ZERO() to detect this situation in advance.
-
The caller must provide temporary memory space in array
tmp[], using macro C4E_ECC2N_TMP_NUM() in conjunction with temp. space qualifier C4E_ECC2N_TMPID_PT2OS. -
The minimum required buffer size (in bytes) for
bufvaries depending the point formatptfmt:* hybrid: 2U *dom->m.len+ 1U * uncompressed: 2U *dom->m.len+ 1U * compressed:dom->m.len+ 1U
- Bibliography:
- Public Key Cryptography For The Financial Services Industry: Key Agreement and Key Transport Using Elliptic Curve Cryptography. ANSI X9.63, 2001.
- Bibliography:
- Standard Specifications For Public-Key Cryptography. Std 1363-2000, IEEE, 2000.
- Parameters:
-
[in] dom Pointer to EC domain parameters. [in] pt Pointer to EC point. [in] ptfmt EC point format: * C4E_EC_PTFMT_PC_C: compressed * C4E_EC_PTFMT_PC_U: uncompressed * C4E_EC_PTFMT_PC_H: hybrid tmp Array of temporary space elements (see preconditions for details on size). Parameter tmpmay be NULL in case the format is pure "uncompressed".[in] bufsize Maximum number of bytes to store in buf(must be greater than zero, else an assert is thrown).[out] buf Output buffer, getting converted EC point pt.
- Returns:
- Number of bytes to represent
pt, 0 on error.
| C4eSysStatus c4e_ecc2n_os2pt | ( | C4E_CONST C4eEcDomain *C4E_RESTRICT | dom, | |
| C4E_CONST C4eArchUint8 *C4E_RESTRICT | osp, | |||
| C4eArchSize | len, | |||
| C4eArchDigit | tmp[C4E_RESTRICT], | |||
| C4eEcPoint *C4E_RESTRICT | pt | |||
| ) |
Octet string to elliptic curve point conversion primitive, according to ANSI X9.63, section 4.3.7 and 4.2.2 and IEEE Std 1363, section A.9.6 and annex E.2.3.
- Note:
- This function cannot convert the pseudo-point at infinity (returns C4E_STATUS_ECODING in that case).
- Precondition:
- The validity of the EC domain parameters in
dommust be assured by the caller, either implicit or by using function c4e_ecc2n_domchk(). -
All binary polynomials in
dommust be normalized, e.g. by using functions c4e_elem_norm() or c4e_elem_os2e(). -
The caller must provide temporary memory space in array
tmp[], using macro C4E_ECC2N_TMP_NUM() in conjunction with temp. space qualifier C4E_ECC2N_TMPID_OS2PT. -
The size of buffers
pt->x.digitsrespectivept->y.digits(in number of digits according topt->x.sizerespectivept->y.size) must be at least:or, when using (maximum) static memory reservation:C4E_ELEM_DIGITS_NUM(dom->m.len)
- Postcondition:
- The coordinate values
pt->xandpt->yare normalized.
- Bibliography:
- Public Key Cryptography For The Financial Services Industry: Key Agreement and Key Transport Using Elliptic Curve Cryptography. ANSI X9.63, 2001.
- Bibliography:
- Standard Specifications For Public-Key Cryptography. Std 1363-2000, IEEE, 2000.
- Parameters:
-
[in] dom Pointer to EC domain parameters. [in] osp Octet string pointer, which represents an EC point, according to the standards mentioned. [in] len Number of bytes in osparray (octet string).tmp Array of temporary space elements (see preconditions for details on size). [out] pt Pointer to EC point, with coordinate digits buffer prepared according to preconditions.
- Returns:
- Conversion result.
- Return values:
-
C4E_STATUS_OK If the octet string was converted successfully. other If conversion of octet string has failed.
- See also:
- C4eEcDomain, C4eEcPoint, C4eElement, C4E_ELEM_ASGN_MEM()
 1.6.1
1.6.1